Trezor Wallet Login: A Comprehensive Guide to Accessing Your Crypto Safely
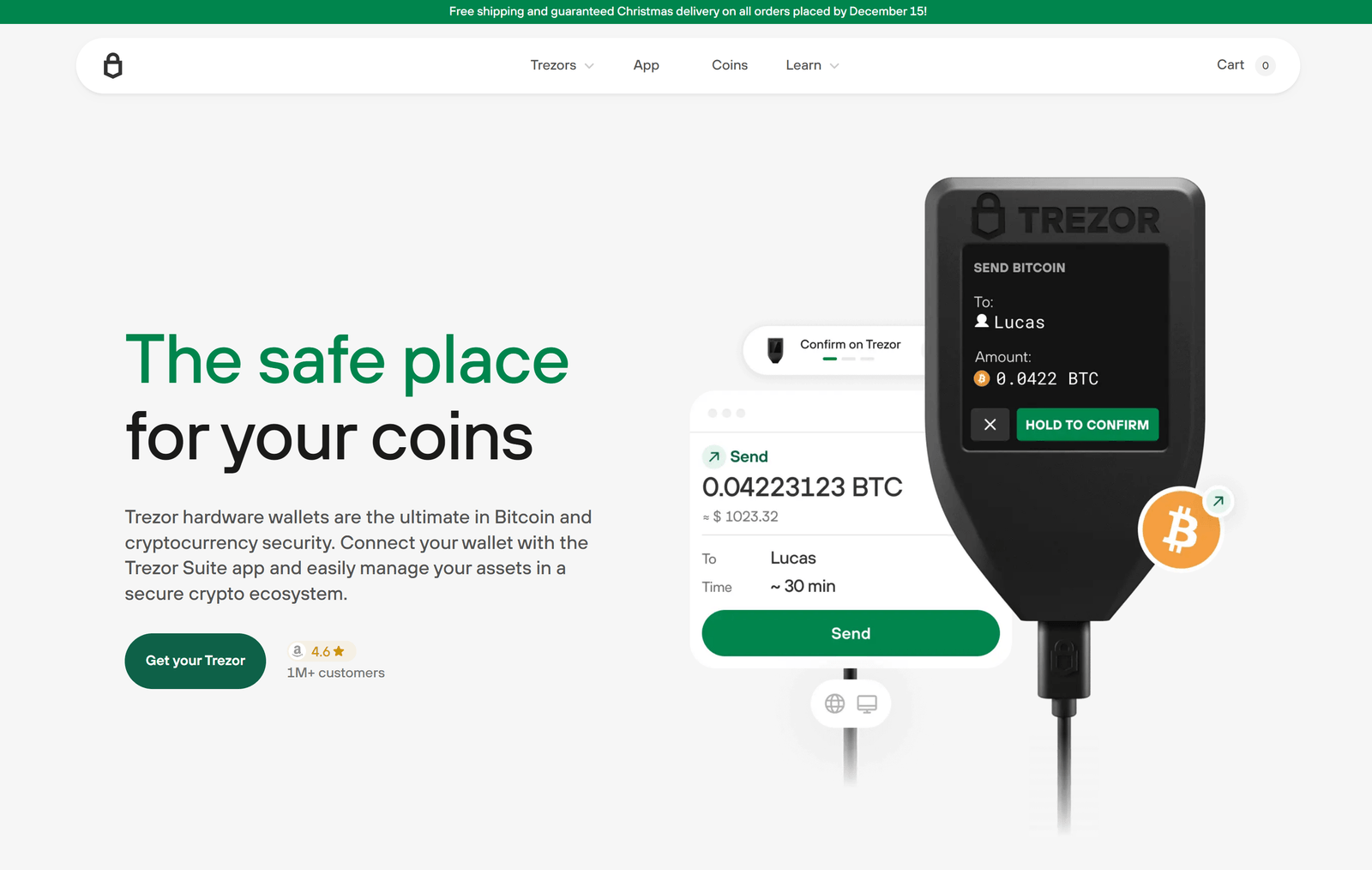
In the evolving world of cryptocurrency, security is paramount. One of the most reliable tools for safeguarding digital assets is the Trezor hardware wallet. Known for its robust security features and user-friendly design, Trezor ensures that your private keys remain offline and protected from potential hacks. However, the first step to managing your crypto assets effectively is mastering the Trezor Wallet login process. This guide will walk you through everything you need to know about logging in safely and efficiently.
Understanding Trezor Wallet
Before diving into the login procedure, it’s essential to understand what a Trezor Wallet is. Trezor is a hardware wallet designed to store cryptocurrency offline. By keeping private keys offline, Trezor prevents unauthorized access and online attacks. It supports a wide range of cryptocurrencies, including Bitcoin, Ethereum, and numerous altcoins, making it a versatile solution for crypto enthusiasts.
Unlike software wallets, which are connected to the internet, Trezor wallets require physical interaction to sign transactions, ensuring an additional layer of security. This makes logging in a slightly different process than traditional software wallets.
Steps to Trezor Wallet Login
Logging into your Trezor wallet is straightforward if you follow the correct steps. Here’s a step-by-step breakdown:
1. Connect Your Trezor Device
Start by connecting your Trezor hardware wallet to your computer using the provided USB cable. Ensure you only use a secure computer and avoid public or shared devices. Once connected, your device will display the Trezor logo and prompt you to proceed with the login process.
2. Visit the Official Trezor Web Interface
Next, open a web browser and go to the official Trezor web interface at trezor.io/start
. Trezor strongly advises users to always access the official site to prevent phishing attacks. Avoid clicking on links from emails or third-party websites claiming to be Trezor.
3. Install Trezor Bridge
For your device to communicate with your computer, you may need to install Trezor Bridge, a small software application. Trezor Bridge ensures secure communication between your wallet and the browser interface. Once installed, the Trezor device will be recognized, allowing you to proceed with login.
4. Enter Your PIN
Your Trezor device is protected by a PIN code. Upon login, your device will prompt you to enter this PIN. The Trezor interface ensures that even if someone is watching your screen, they cannot discern your PIN due to a randomized keypad on the device itself. Enter the correct PIN to continue.
5. Enter Your Passphrase (Optional)
For added security, Trezor supports a passphrase feature. If you have enabled a passphrase, you will be prompted to enter it during the login process. This acts as an additional layer of protection, effectively creating a “hidden wallet” within your Trezor device.
6. Access Your Wallet Dashboard
Once your PIN and passphrase are verified, you will gain access to your Trezor wallet dashboard. Here, you can view your cryptocurrency balances, initiate transactions, and manage your assets safely. The Trezor interface is user-friendly, allowing you to navigate between accounts, view transaction history, and send or receive funds effortlessly.
Security Tips for Trezor Wallet Login
Logging into your Trezor wallet involves handling sensitive information, so adhering to best security practices is crucial:
- Always use the official Trezor website: Avoid phishing attempts and double-check URLs.
- Never share your PIN or recovery seed: Trezor support will never ask for this information.
- Keep your recovery seed offline: Store it securely in a safe location, separate from your device.
- Enable passphrase protection: This adds an extra layer of security for high-value accounts.
- Update your firmware regularly: Trezor frequently releases updates to improve security and functionality.
Troubleshooting Login Issues
Sometimes, users may encounter login difficulties. Common issues include:
- Device not recognized: Ensure Trezor Bridge is installed and your USB connection is stable.
- Incorrect PIN: After multiple failed attempts, the device may reset for security reasons. Use caution when entering your PIN.
- Browser compatibility: Trezor works best with modern browsers like Chrome or Firefox. Clear cache if necessary.
In case of persistent problems, consult the official Trezor support page
for guidance.
Conclusion
The Trezor Wallet login process is designed with security and user convenience in mind. By following the steps outlined above and adhering to best security practices, you can ensure that your digital assets remain safe and accessible. Remember, your Trezor hardware wallet is only as secure as the precautions you take. Always keep your PIN, passphrase, and recovery seed confidential, and use official channels for login and updates. With Trezor, managing your cryptocurrency can be both safe and straightforward.