Securely Access Your Crypto: A Complete Guide to Trezor Login
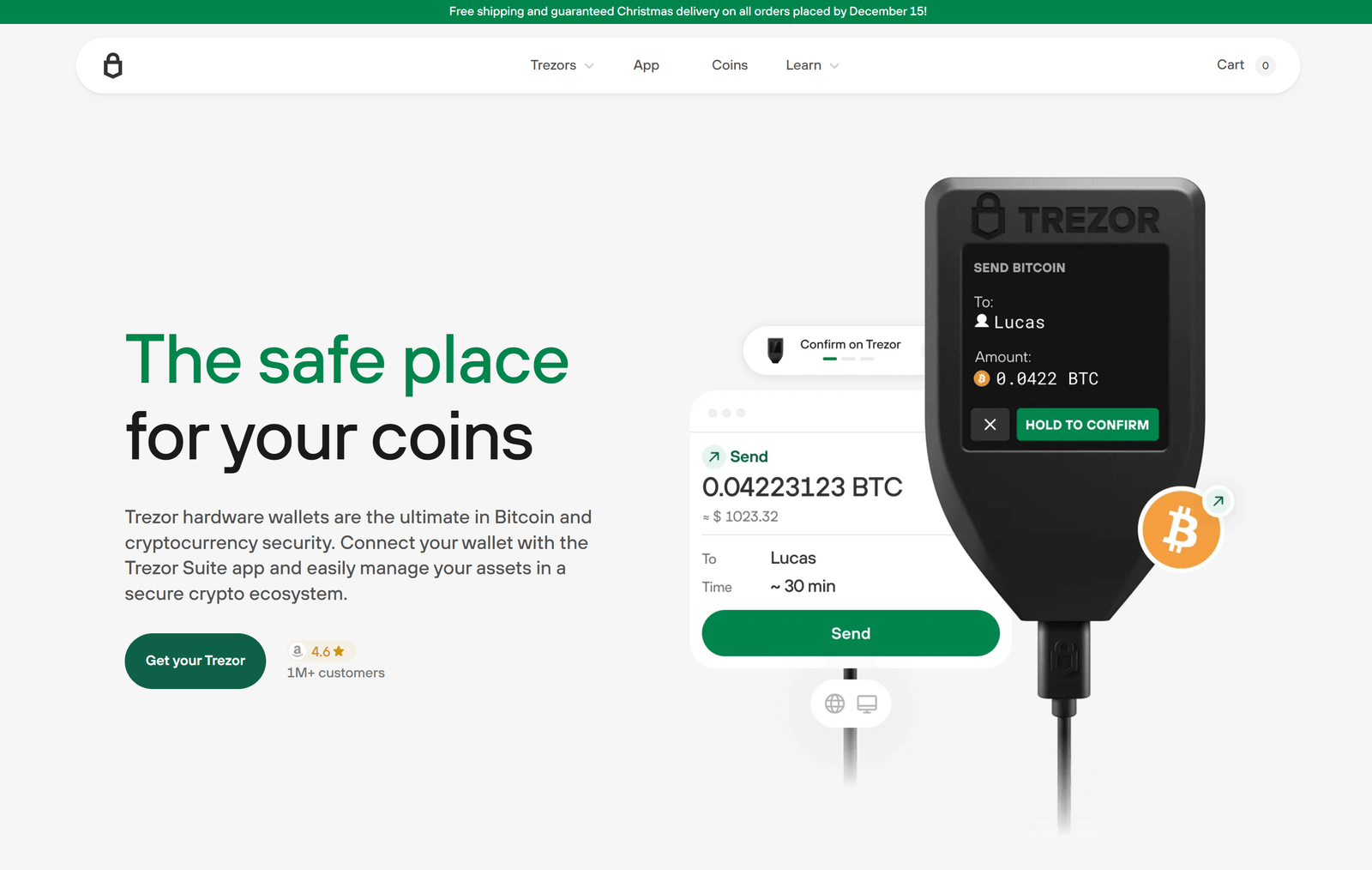
In the fast-evolving world of cryptocurrency, security is paramount. Managing digital assets safely requires reliable tools, and one of the most trusted names in hardware wallets is Trezor. Trezor hardware wallets, known for their robust security and user-friendly interface, offer a secure way to store and manage cryptocurrencies. However, to access your assets, understanding the Trezor login process is essential. In this guide, we will walk you through everything you need to know about Trezor login, from setup to troubleshooting, ensuring your crypto remains safe and easily accessible.
Understanding Trezor and Its Importance
Trezor is a hardware wallet developed by SatoshiLabs that stores private keys offline, keeping your crypto safe from hackers and malware. Unlike software wallets, which are vulnerable to cyber-attacks, Trezor provides a cold storage solution, meaning your private keys never leave the device. Logging in to your Trezor wallet is your gateway to securely managing assets like Bitcoin, Ethereum, and hundreds of other supported cryptocurrencies. The login process might seem straightforward, but mastering it ensures smooth transactions and prevents security mishaps.
Preparing for Trezor Login
Before logging in, you need to have your Trezor device set up correctly. Follow these steps to prepare:
- Unbox and Inspect Your Device: Make sure the Trezor device you received is genuine. Always buy from official channels like Trezor.com
- to avoid counterfeit devices.
- Install Trezor Bridge: Trezor Bridge is a communication tool that connects your Trezor device to your computer. Download and install the latest version from the official website.
- Connect Your Device: Use the USB cable to connect your Trezor to your computer. Ensure that the connection is secure.
- Update Firmware: If prompted, update your device firmware. Firmware updates improve security and functionality. Never skip this step.
Once your device is ready, you are prepared for the login process.
Step-by-Step Guide to Trezor Login
Logging in to your Trezor wallet is simple yet secure. Here’s a detailed step-by-step guide:
- Visit Trezor Suite or Trezor Web Interface: The Trezor Suite app or web interface allows you to manage your crypto. Access the official Trezor login portal at trezor.io/start
- .
- Connect Your Device: Plug in your Trezor device and select the appropriate option in the Suite or web interface.
- Enter Your PIN: Your Trezor PIN ensures that even if someone has physical access to your device, they cannot access your crypto. The PIN is input through a randomized touchscreen grid on your computer, making it immune to keyloggers.
- Enter Your Passphrase (Optional): For added security, Trezor allows the use of a passphrase. This acts as an extra layer of protection for your wallet. Remember, losing your passphrase may result in losing access to your assets.
- Access Your Wallet: After PIN and passphrase verification, you will be successfully logged in. You can now view your balances, send and receive cryptocurrencies, and manage your portfolio securely.
Common Login Issues and Troubleshooting
Even with Trezor’s intuitive interface, users may encounter login issues. Here are some common problems and solutions:
- Device Not Detected: Ensure Trezor Bridge is installed and running. Try reconnecting the device and using a different USB port.
- Forgot PIN: Enter the recovery seed on a new Trezor device to reset access. Never share your recovery seed with anyone.
- Browser Compatibility Issues: Trezor works best with Chrome, Firefox, or Brave browsers. Clear cache or update your browser if problems persist.
- Passphrase Mistakes: Double-check spelling and capitalization. A passphrase is case-sensitive, and incorrect entry may lock you out temporarily.
By understanding these common issues, you can quickly resolve login challenges without compromising security.
Enhancing Your Trezor Login Security
While Trezor is inherently secure, adopting best practices ensures maximum protection:
- Use a Strong PIN and Passphrase: Avoid obvious numbers like birthdays.
- Keep Recovery Seed Offline: Store your 12- or 24-word recovery seed in a safe, offline location.
- Update Firmware Regularly: Trezor releases updates to counter emerging security threats.
- Beware of Phishing Attacks: Always visit the official Trezor site. Avoid clicking suspicious links or emails claiming to be Trezor support.
Following these steps ensures that your login remains secure, giving you peace of mind while managing your digital assets.
Conclusion
Trezor login is more than just accessing your cryptocurrency—it is the gateway to security, control, and peace of mind. By understanding the setup process, login steps, troubleshooting methods, and security best practices, you can ensure your crypto experience is smooth and safe. With Trezor, your digital assets remain protected from hackers, malware, and online threats. Whether you are a beginner or an experienced crypto holder, mastering Trezor login is crucial for a secure and efficient crypto journey.
For official guidance and downloads, visit Trezor Start
to get your Trezor wallet up and running today. Safeguard your assets, take control of your crypto, and enjoy the confidence that comes with using one of the most trusted hardware wallets in the market.